The Emergence And Evolution Of Cloud And Web Enabled Threats

The world is changing rapidly and so is our internet usage. Traditionally, the internet was all about browsing websites which have now changed majorly to the usage of SaaS applications. HTTP browsing has changed to 90% of HTTPS traffic and API communication. On-prem apps hosted in the customer’s data center are moving to public clouds like AWS, Azure, and Google Cloud. Web-based attacks over the years have gained prominence with adware, malware, and phishing on the rise.
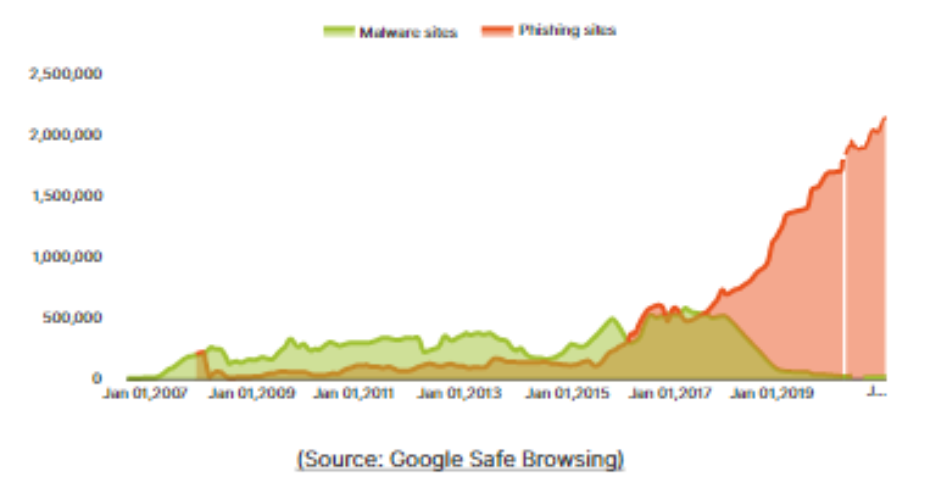
The below chart indicates the rise in phishing sites as per Google until Jan 2021.
Remote working has only made this problem worse. As per a repot from Kaspersky, Bute force attacks on RDPs (Remote Desktop Protocol) skyrocketed to 3.56 billion globally and reached 15.8 million in the UAE alone. Adversaries are always ahead in adopting the technological curve, and thus we see the usage of modern technologies in the way hackers plan attacks. Increasing crackdown on phishing and malicious sites is making it harder for hackers to attack and thus adversaries are finding new ways to lure victims.
One of the prominent ways is the usage of cloud and SaaS services. Instead of using new domains and URLs, now adversaries use cloud services like AWS/Azure/GCP and SaaS apps like Box, Webmail, OneDrive, etc. to preform malicious activities. Most organizations do not block these trusted apps and thus fall victim to these attacks. Cloud-delivered campaigns could be used against any user regardless of what type of device they are on. Campaigns with that type of flexibility often have a greater chance of success, especially if they hit a target on a mobile device where it is harder to spot phishing attacks.
Adversaries craft these attack campaigns utilizing cloud apps primarily for four objectives:
Delivery: Cloud service is used to deliver malware or host a phishing page
Examples from recent past:
18 Jun 2021 – Using Google Docs
In this campaign, attackers used Google Docs to host a phishing page.
As most of the organizations do not block Google Docs, the phishing page was accessible, and a lot of victims fell prey to these attacks.
12 Jan 2021 – Using Coronavirus-related info as a lure
In this incident, targeted users are redirected to a Google Form landing page hosting the malicious website. A legitimate Google–registered URL can often convince even security-conscious users into handing over their information. The aesthetics of this campaign are solid and simple enough to reach users in environments protected by secure email gateways (SEGs).
Exploitation: The cloud service is exploited to steal data, or launch other attacks
Examples from recent past:
10 June 2021 – EA games were hacked using Slack
The process stated by purchasing stolen cookies being sold online for $10 and using those to gain access to a Slack channel used by EA.
9 June 2021 – Crypto-mining attacks on Azure Kubernetes clusters
Microsoft wans of an ongoing series of attacks compromising Kubernetes clusters running Kubeflow machine leaning (ML) instances to deploy malicious containers that mine for Monero and Ethereum cryptocurrency.
2 May 2021 – Microsoft wans of increasing OAuth Office 365 phishing attacks
An application-based attack variant was observed where the attackers attempt to tick targets into providing malicious Office 365 OAuth apps (web apps registered by the attackers with an OAuth 2.0 provider) with access to their Office 365 accounts.
30 Mar 2021 – Upstox wans of a serious data breach on AWS
Customers’ names, contact information, date of birth, bank account information, and millions of KYC (Know Your Customer) details are believed to have been stolen by the ShinyHunters gang after they gained access to the company’s Amazon AWS key.
Command and Control: The cloud service is exploited as a Command-and-Control infrastructure
Examples from recent past:
22 Apr 2021 – Using Telegram for C&C
Malware authors are using the Telegram platform as an out-of-the-box command and control system for malware distribution into organizations. This system allows the malware to receive future command and control instructions remotely using Telegram, even when Telegram is not in use.
12 Jan 2021 – Abusing Google and Microsoft to host C&C
Infrastructure Hackers stated using sub-domains under the parent domain appspot.com and azureedge.net in 2019 for hosting C&C infrastructure. The parent domain appspot.com is a domain owned by Google, and pat of Google’s App Engine platform as a service. Azureedge.net is a parent domain owned by Microsoft, and pat of Microsoft’s Azure content delivery network.
Data Exfiltration: The cloud service is used to store the exfiltrated data
Examples from recent past:
26 Mar 2021 – Using S3 buckets to store exfiltrated data
Hackers gained access to the Microsoft 365 environment of SalusCare, a provider of behavioral healthcare services in Southwest Florida. Hackers downloaded sensitive data and uploaded the stolen data to two Amazon S3 storage buckets.
12 Jan 2021 – Dropbox, G-dive, and One-dive abused to store exfiltrated data.
Adversaries were using a custom tool to compress and encrypt the data before securely exfiltrating it in allowed applications of the organization (i.e. Dropbox, Google, Microsoft).
Recommendations
With assets (i.e. data, identities, and applications) moving to the cloud, it becomes imperative to deploy security controls in the cloud as well. The solution should provide the capability to gain deeper visibility in cloud apps in addition to IaaS and PaaS environments so that modern cloud and web-enabled threats can be tackled. Help AG’s recently launched Cyber Edge X, a SASE based security offering is one such offering.
Cyber Edge X aims to simplify network security with the unification of perimeter security products like Secure Web Gateway, CASB, DLP and FWaaS delivered with one console, one agent approach, as well as unified threat protection through one single threat dashboard with advanced analytics delivering features like UEBA and ATP across all the network’s perimeter controls. With its local presence in Etisalat data centers in UAE, the solution provides the least latency path to reach applications with compliance to local UAE regulations.






